NIS2 and Visitor Management System
- Home
- Our products
- Visitor Management System
Navigate the complexity of the NIS2 directive with our comprehensive guide. Discover why it’s important for sectors such as government, defense, energy, healthcare, and IT, and learn how PartnerSec’s visitor management solutions can help you comply with the NIS2 directive.
Fill out our form and we will help you with all your questions:
1. What?
2. Who?
3. Your message
- Automated visitor management
- Professional treatment
- Customer tailored experience
What is NIS2 and how does it affect your organization?
In the digital era, terms like cyberattacks, phishing, malware, and ransomware are more than just trendy buzzwords. They represent real threats that affect our daily lives. As our society becomes increasingly dependent on digital infrastructure, the challenge of safeguarding it has never been greater. That’s why Europe created the NIS2 directive, a powerful initiative to strengthen cybersecurity in Europe.
The new cybersecurity legislation, NIS2, redefines the rules regarding risk management and reporting requirements and introduces stricter penalties for non-compliance.
October 17, 2024, is the deadline by which EU countries must transpose NIS2 into their national laws, meaning that all affected organizations must prepare for a significant review of their cybersecurity measures. How will this affect your business? And how should you prepare for the changes ahead?
In this article, we will cover everything you need to know about the new legislation and explore its implications for your company. We will address the following key questions:
What is NIS2?
The NIS2 directive (in full: the Network and Information Security Directive 2022/0383) is the cornerstone of EU-wide legislation on cybersecurity. Its purpose is to enhance the security of networks and information systems in Europe. It requires operators of critical infrastructure and providers of essential services to implement necessary security measures and report incidents to the authorities.
NIS2 is an update of the original NIS1 directive from 2016, and it came into force in January 2023. EU member states have until October 17, 2024, to transpose the directive into national legislation. This means that every organization falling within its scope will be legally obliged to comply with its requirements by the end of 2024. Overall, NIS2 involves more than 160,000 organizations across Europe.
How does the visitor management system CavVisit help your organization comply with NIS2?
One of the cornerstones of NIS2 is data traceability and the ability for efficient reporting. When an incident occurs, NIS2 stakeholders must be able to generate a report on which individuals were present at the facility/office when the incident occurred, as well as the time leading up to the incident and the data associated with them. All visitors are registered in CavVisit, providing NIS2 personnel with the ability to export visitor data in a report-friendly format to serve as the basis for NIS2-compliant reporting.
The visitor system is designed to be easily configured to include the correct NIS2 data fields for all visitors. By ensuring that all visitors fill in the data fields required by your organization, you can guarantee compliance with the traceability requirements that NIS2 imposes on your organization.
CavVisit’s visitor kiosks are configured to ensure that visitors fill in all data fields correctly and agree to the visitor policy, which includes both GDPR information and information from the visitor system’s NIS2 data fields. Different facilities will have different data requirements regarding NIS2, and this is something that is configured within the visitor system. These data fields are tailored to the specific facilities/offices using CavVisit’s built-in multi-site functionality.
Open Wi-Fi networks, known as guest networks, do not meet NIS2 requirements as they do not require visitors to provide login credentials, allowing the visitor’s cyber traffic to be traced. With CavVisit’s Wi-Fi integration with HP Aruba, Cisco, and Ubiquiti Wi-Fi platforms, each visitor receives unique login credentials for the guest network, allowing NIS2 stakeholders to see exactly how visitors have used the guest network.
What is new with NIS2?
Compared to NIS1, the scope of the legislation has been significantly expanded. Additionally, mandatory security measures and incident reporting have been tightened, and the consequences for non-compliance are much stricter.
Which organizations and companies are affected by NIS2?
Does your organization fall within the scope of the NIS2 directive?
Let’s first look at the 18 sectors covered by NIS2. The directive divides these into two categories: “highly critical” and “other critical.” The main difference lies in the supervisory measures and penalties; we will come back to this later. However, organizations in both categories must meet the same requirements.
18 sectors and types of organizations affected by NIS2
These sectors are classified as HIGHLY critical:
- Banking sector
- Transport sector
- Healthcare
- Government agencies
- Energy sector
- Financial sector
- Water and sewage
- Digital infrastructure and Telecom
- Space sector
The sectors classified as OTHER critical are:
- Manufacturing and distribution of chemicals
- Manufacturing and distribution of food
- Waste management
- Postal and courier services
- Manufacturing of medical equipment, computers, electronics, heavy machinery and equipment, motor vehicles, trucks and light trucks, and other transport-related equipment.
- Digital service providers
- Research and development
If your business or sector is included in any of the listed sectors, you are likely affected by NIS2.
Please note! There is another level beyond these 18 sectors. NIS2 also defines two categories of organizations that must comply with the legislation: “essential” and “important” entities.
Does your organization fall under the influence of NIS2? See the chart below.
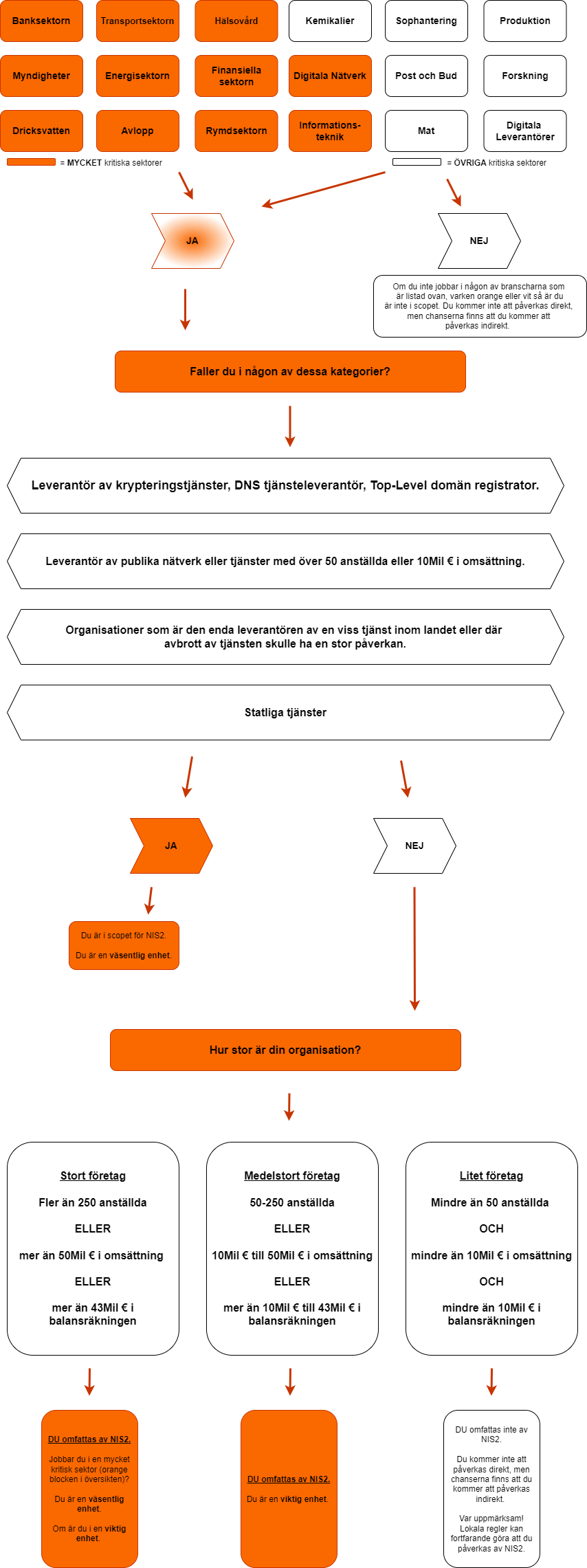
2 categories of entities in NIS2
Essential entities
- Organizations in “highly critical” sectors with more than 250 employees or an annual turnover of more than 50 million euros or a balance sheet total exceeding 43 million euros.
- Trust service providers, top-level domain registries, and DNS service providers, regardless of their size.
- Providers of public electronic communications networks or services with 50-250 employees or more than 10 million euros in revenue.
- Government/Public services (central level).
- All other important organizations that are the sole provider of the service within the country, or where interruptions in their service may have a significant impact.
Important entities
- Organizations within “other critical” sectors with more than 50 employees or an annual turnover of more than 10 million euros.
- Organizations in “highly critical” sectors with 50-250 employees or an annual turnover of 10 to 50 million euros or a balance sheet total of 10 to 43 million euros.
Small businesses with fewer than 50 employees and turnover of less than 10 million euros are not automatically excluded. Member states may consider them “critical” or “important” if their services play a key role in society or if interruptions in their services would have significant consequences for public health or safety.
Important entities can be proactively checked for compliance with NIS2, while important entities are only investigated after a complaint.
If your organization is outside the EU?
If your organization is not based in the EU, you might think that NIS2 doesn’t apply to you. Unfortunately, if your organization falls under any of the previously mentioned categories and provides services within the EU, you must comply with the NIS2 directive.
The NIS2 directive sets out specific guidelines for organizations outside the EU. Entities outside the EU providing services within the EU are required to appoint a representative in an EU member state where the services are provided. This person must oversee the organization’s compliance with NIS2. Your organization should have a designated NIS2 responsible person.
What happens if your organization falls outside the scope?
If your organization is not within the scope of NIS2, you don’t need to worry about fines or immediately following the rules. However, there’s a good chance you’ll still be affected by NIS2.
For example, if you provide services or products to an entity within the scope of NIS2, that client may require you to meet a certain level of cybersecurity. In this case, you won’t be audited by authorities monitoring NIS2 compliance, but rather by your client.
It may still be wise to consider aligning your security measures with the NIS2 directive. This approach makes it easier to collaborate with other businesses, and you can assure your clients that you are compliant and reliable.
What are the NIS2 requirements?
So your organization falls within the scope of the NIS2 directive. What does this mean for you and what is the next step?
1. Registration
By April 17, 2025, member states must identify all essential and important entities falling within the scope of NIS2. Details about the registration process will be finalized once the directive has been transposed into national legislation. At minimum, the registration will include the following information:
- Name, address, and registration number
- Sector
- Contact information
- Member states where the organization operates
- Assigned IP addresses
2. Obligations
This brings us to the main question: what actions and obligations exist for organizations within the scope of NIS2? NIS2 divides the requirements into four main areas:
- Risk management: Companies should take measures to minimize cyber risks, such as incident management, stronger supply chain security, improved network security, better access control, and encryption.
- Accountability: Management should be trained and must oversee the organization’s cybersecurity measures and manage risks; breaches can lead to sanctions.
- Reporting: Organizations must have processes in place to promptly report significant security incidents.
- Continuity: Organizations should plan how to ensure business continuity in the event of cyber incidents.
3. 10 minimum security measures
In addition to these four main areas, NIS2 provides 10 basic security measures for important and essential entities:
- Risk analysis and information system security.
- Evaluation of security measures.
- Policies and procedures for the use of cryptography and, when relevant, encryption.
- An incident management plan.
- Security in acquisition, development, and maintenance of networks and information systems, including vulnerability reporting.
- Cybersecurity training and basic practices for cyber hygiene.
- Access policies and security procedures for employees with access to sensitive or critical data.
- A business continuity plan during and after a security incident.
- The use of multi-factor authentication or continuous authentication solutions and encryption of communication.
- Security in supply chains and relationships with suppliers.
4. New reporting requirements
Let’s hope you don’t need this section, but if a security incident occurs, you must notify the appropriate authorities. Here are the new guidelines:
- Within 24 hours: an “early warning” to the Computer Security Incident Response Team (CSIRT) or national authority.
- Within 72 hours: an incident notification with an initial assessment of the incident, its severity, and consequences.
- Within 1 month: a final report with a detailed description of the incident, including its severity, impact, cause, and actions taken.
5. What penalties and fines are in place?
The NIS2 directive defines two categories for organizations within its scope. Don’t worry if you can’t see the forest for the trees: here’s a brief summary.
- Essential entities are large organizations (>250 employees or >50 million euros in revenue) in sectors such as transport, energy, water, and space.
- Important entities are medium-sized organizations (>50 employees or >10 million euros in revenue) in the aforementioned sectors; AND large and medium-sized organizations in sectors such as food, digital services, and research.
The requirements for both categories are the same; the difference lies in the supervisory measures and sanctions, which the tables below illustrate.
Fines
Essential entities
Important entities
Fines:
10 million euros or 2% of the global annual turnover.
Non-monetary penalties:
– Compliance orders
– Binding instructions
– Implementation orders for security audits
– Orders to notify threats to entities’ customers
– Criminal penalties for management
Fines:
7 million euros or 1.4% of the global annual turnover.
Non-monetary penalties:
– Compliance orders
– Binding instructions
– Implementation orders for security audits
– Orders to notify threats to entities’ customers
– Criminal penalties for management
Please note! Member states may prescribe that fines do not apply to government bodies. However, the other penalties will still apply.
Supervisory measures
Essential entities
Important entities
Active controls:
External audits, inspections, documentation requests.
Post-supervision:
Actions taken when authorities obtain evidence of non-compliance.
6. How to prepare your business for NIS2
What’s next for your organization?
If you’re not within the scope, you can breathe easy. But you’re not completely exempt. Make a list of companies you work with that must comply with NIS2 and consider what this means for your organization. And think about whether and how you can still apply the new security measures, as they will ultimately benefit you.
If you’re within the scope, it’s time to get to work. We recommend following these steps to get started with NIS2 preparations:
- Conduct a risk assessment. What are the potential security risks? How likely are they to occur? What is the potential impact? And what measures are already in place to mitigate the risks?
- Update your security policies. Based on the risk assessment, update existing security policies or develop new ones. Make sure you cover the 10 basic requirements of NIS2.
- Implement security measures. Options include: enhanced network security, stricter access controls, encryption, and securing the supply chain. Our automated visitor management system, CavVisit, can help you significantly: it provides control over your visitor management, securely stores visitors’ personal data, and simplifies incident reporting by maintaining accurate records of all visitors’ activities.
- Develop procedures for detecting, monitoring, resolving, and reporting incidents.
- Train your staff and management. Which employees perform critical functions within the organization? Make them aware of the risks and security measures.
- Prepare for audits and inspections. Maintain clear and comprehensive records of your security policies, risk assessments, incident reports, and compliance activities.
Conclusion
The NIS2 directive represents a milestone in the European Union’s policy to strengthen cybersecurity standards within its borders. For organizations falling under this regulation, complying with NIS2 is not just a legal obligation, but also an opportunity to improve their cybersecurity, protect their data, and build trust with customers and partners.
The directive requires a proactive approach, and the adoption of a digital visitor management system plays a key role in this context. Such a system helps to comply with NIS2 standards in several ways. It enhances access control and protects visitors’ personal data from cyber threats. Additionally, the system maintains accurate logs of visitors’ activities, simplifying the assessment of potential risks, strengthening supply chain security, and facilitating incident management and reporting in the event of a security incident.
To get a sense of how a modern visitor management system can benefit your business, contact us today. Chat with us or book a demo to discuss how PartnerSec can help you improve your visitor management.
Receive visitors automatically
The cloud-based visitor management system CavVisit has a built-in rule engine where visit processes are customized for each installation and location. Each location has its own unique rules to automatically handle visitors.

QR codes to your mobile phone
In the automated booking process, we send QR codes to visitors’ mobile phones via SMS. The visitor no longer needs a visit badge; instead, they use their mobile phone and show the QR code to the QR code reader.
Matching the right visitor to the right floor
The automatic QR code solution automatically guides the visitor to the correct floor through an integration with the elevators in the building. The QR code only works on the floors that the visitor is authorized to access.

The smart choice
Automatic updates, web-based interfaces, built-in schedules, automated GDPR/NDA processes, encryption, mobile keys, and much more make PartnerSec the right choice for unmanned receptions looking to use modern security solutions.
CavVisit's features
PartnerSec’s visitation system includes a range of features tailored to the needs of each business.
QR code-based Check-in and Identification
A QR code-based check-in enables visitors to quickly and easily register upon arrival. Visitors should be able to generate or receive QR codes in advance and then scan them at a visitor kiosk or a QR code reader at the entrance. This allows for a seamless and contactless check-in process, minimizing queues and increasing efficiency.
Authorization Control and Access Management
The automatic reception should have a mechanism to ensure that only authorized visitors gain access to specific areas or buildings. This can be achieved by linking QR codes to visitors’ permissions. When the QR code is scanned, the system should automatically verify the visitor’s permissions and grant the appropriate access. This is particularly important for companies with different security levels and restrictions for various areas.
Visitor logging and security tracking
A central function is to log visitors’ activities and information. Visitor logs include the time of check-in, name, contact details, and purpose of the visit. These details are not only important for ensuring security but also for tracking and monitoring visitor patterns. If something unexpected occurs, the organization can easily trace visitors and contact them if necessary.
Customizability and Integration
The automatic reception should be customizable to fit the specific needs and requirements of the company. It should be possible to integrate the system with existing security and network infrastructures. Additionally, it should be scalable to meet future demands and technological advancements. Integration with other systems, such as network access control, can also be an important feature to provide a comprehensive solution for visitor management.